Technology
GitHub Copilot Vulnerability Exposes Sensitive Data to Attackers

A critical vulnerability in GitHub Copilot Chat has been identified, allowing attackers to silently extract sensitive data from private repositories. The flaw, which has a CVSS score of 9.6, enables malicious actors to manipulate the AI assistant’s responses and potentially compromise intellectual property and cloud credentials. GitHub has issued a fix for this vulnerability.
Security researcher Omer Mayraz highlighted the severity of the issue, noting that the vulnerability facilitated “silent exfiltration of secrets and source code from private repos.” This situation poses significant risks for software organizations that utilize AI assistants for code review and pull request (PR) triage.
Details of the Attack
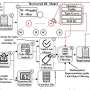
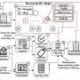
The attack was initiated by embedding an attacker-controlled prompt within a pull request description using GitHub’s “invisible comments” feature. Although these comments are not visible in the standard user interface, Copilot Chat still accesses the repository and PR context, including hidden metadata. The AI assistant operates under the permissions of the user querying it, meaning that malicious instructions can influence its behavior for any developer engaging with that PR.
By leveraging this permission model, attackers can instruct Copilot to search for sensitive artifacts, such as API keys and vulnerability descriptions, within the victim’s accessible repositories. The findings could then be rendered or encoded into output that is exfiltrated without triggering conventional network security measures.
Evading Security Protocols
GitHub has implemented a Content Security Policy (CSP) to block direct data leakage to external domains. To circumvent this, attackers created pre-signed proxy URLs that pointed to benign 1×1 transparent pixel images hosted on their infrastructure. By assembling a dictionary of signed proxy URLs, attackers could manipulate the output generated by Copilot to encode repository content.
The injected prompt coerced Copilot to produce output that referenced these pre-signed proxy URLs in a specific sequence, effectively transmitting sensitive data back to the attackers. Each request for these images, which were fetched through GitHub’s Camo proxy, bypassed traditional data logs and security systems, as they appeared to be normal GitHub activity.
Furthermore, attackers employed evasion techniques by appending ephemeral query parameters to each URL. This tactic ensured that each fetch represented new data and reduced the likelihood of exfiltrated content appearing in server logs.
Mitigating Future Risks
To protect against similar vulnerabilities in AI-assisted technologies, organizations should adopt a comprehensive approach that includes access control, identity protection, and ongoing monitoring. Recommended measures include:
– **Restrict Access and Permissions**: Limit use of Copilot to essential teams and repositories, applying the principle of least privilege and disabling unverified features such as image or HTML rendering.
– **Enhance Identity and Secrets Management**: Implement multi-factor authentication (MFA), regularly rotate secrets, and monitor for unauthorized access or misuse of credentials.
– **Monitor, Detect, and Respond**: Actively track Copilot activity, investigate any anomalies, and incorporate AI compromise scenarios into incident response plans.
– **Educate Developers**: Train developers to consider PR content as untrusted, conduct thorough reviews of AI-generated code, and block unverified external rendering.
These strategies can help organizations reduce exposure to vulnerabilities while ensuring that AI-assisted development remains secure and innovative.
As AI tools become increasingly integrated into developer platforms, the potential for exploitation grows. Issues like this underscore the necessity for enterprises to treat AI assistants as privileged integrations. Mapping data flows, constraining capabilities, and prioritizing rapid vendor-led mitigations are essential steps in safeguarding sensitive information.
The CamoLeak incident serves as a stark reminder that while AI technology can enhance productivity, it also presents new avenues for threats. Developers and organizations must remain vigilant as the landscape continues to evolve.
-

 Science2 months ago
Science2 months agoNostradamus’ 2026 Predictions: Star Death and Dark Events Loom
-

 Science3 months ago
Science3 months agoBreakthroughs and Challenges Await Science in 2026
-

 Technology3 months ago
Technology3 months agoOpenAI to Implement Age Verification for ChatGPT by December 2025
-

 Technology6 months ago
Technology6 months agoElectric Moto Influencer Surronster Arrested in Tijuana
-

 Technology8 months ago
Technology8 months agoDiscover the Top 10 Calorie Counting Apps of 2025
-

 Health6 months ago
Health6 months agoBella Hadid Shares Health Update After Treatment for Lyme Disease
-

 Health6 months ago
Health6 months agoAnalysts Project Stronger Growth for Apple’s iPhone 17 Lineup
-

 Technology3 months ago
Technology3 months agoTop 10 Penny Stocks to Watch in 2026 for Strong Returns
-

 Health6 months ago
Health6 months agoJapanese Study Finds Rose Oil Can Increase Brain Gray Matter
-

 Science5 months ago
Science5 months agoStarship V3 Set for 2026 Launch After Successful Final Test of Version 2
-

 Education6 months ago
Education6 months agoHarvard Secures Court Victory Over Federal Funding Cuts
-

 Health6 months ago
Health6 months agoErin Bates Shares Recovery Update Following Sepsis Complications