Technology
Cybercriminals Revive DarkComet Spyware as Fake Bitcoin Wallet
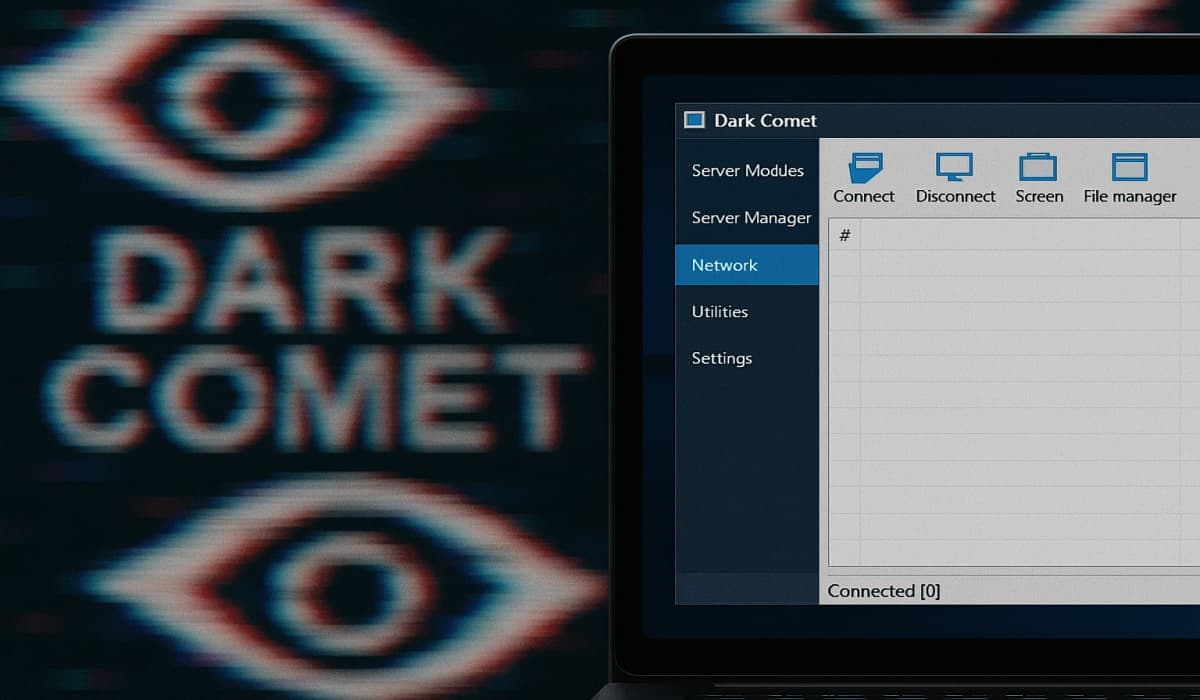
Cybercriminals have resurfaced the notorious DarkComet RAT, a piece of spyware originally developed in 2008, cleverly disguised as a fake Bitcoin wallet application. The malware was identified by the Lat61 Threat Intelligence Team at Point Wild, highlighting the ongoing risks associated with cryptocurrency and digital security. This incident illustrates how outdated malicious software can be repackaged to exploit contemporary trends.
The DarkComet Remote Access Trojan (RAT) allows hackers to gain complete and covert control over a victim’s computer. It features capabilities such as keylogging, file theft, and even webcam surveillance. The malware has a notorious history, being referenced in the WikiLeaks Vault 7 data leak, which revealed its use by both the American CIA and the Syrian government to infiltrate the devices of their citizens.
Malware Delivery and Evasion Techniques
The recent variant of DarkComet was delivered in a compressed RAR file, a common tactic employed by cybercriminals to bypass security protocols and entice users to open the file. Upon extraction, the file was identified as “94k BTC wallet.exe.” Further analysis uncovered that the file was “packed” using a technique known as UPX, which conceals the malicious code, making it difficult for standard security measures to detect the threat until it executes.
Once activated, the DarkComet RAT embeds itself into a hidden system folder and establishes an autostart entry, ensuring it launches automatically with every system boot. It then connects to a specific remote server, kvejo991.ddns.net, on port 1604, enabling ongoing communication with the attacker to receive commands.
Risks and Implications for Cryptocurrency Users
The primary objective of this malware is evident in its keylogging functionality, which records every keystroke made by the victim and saves this information in a local folder labeled dclogs. Such logs can contain sensitive data, including passwords, banking information, and, crucially, access credentials for Bitcoin wallets. This poses a significant risk of financial loss for victims.
The findings from this investigation were shared with Hackread.com, underscoring the importance of downloading cryptocurrency wallets and trading applications only from verified and reputable sources. Dr. Zulfikar Ramzan, Chief Technology Officer of Point Wild and head of the Lat61 team, emphasized the continued threat posed by old malware, stating, “Old malware never truly dies – it just gets repackaged. DarkComet’s return inside a fake Bitcoin tool shows how cybercriminals recycle classic RATs to exploit modern hype.”
This resurgence of DarkComet serves as a critical reminder for individuals involved in digital currencies to remain vigilant. As cybercriminals adapt their strategies to incorporate familiar tools into new scams, the need for robust cybersecurity measures is more pressing than ever.
-

 Science1 month ago
Science1 month agoNostradamus’ 2026 Predictions: Star Death and Dark Events Loom
-

 Technology2 months ago
Technology2 months agoOpenAI to Implement Age Verification for ChatGPT by December 2025
-

 Technology7 months ago
Technology7 months agoDiscover the Top 10 Calorie Counting Apps of 2025
-

 Health5 months ago
Health5 months agoBella Hadid Shares Health Update After Treatment for Lyme Disease
-

 Health5 months ago
Health5 months agoAnalysts Project Stronger Growth for Apple’s iPhone 17 Lineup
-

 Technology5 months ago
Technology5 months agoElectric Moto Influencer Surronster Arrested in Tijuana
-

 Education5 months ago
Education5 months agoHarvard Secures Court Victory Over Federal Funding Cuts
-

 Health5 months ago
Health5 months agoErin Bates Shares Recovery Update Following Sepsis Complications
-

 Technology6 months ago
Technology6 months agoDiscover How to Reverse Image Search Using ChatGPT Effortlessly
-

 Technology7 months ago
Technology7 months agoMeta Initiates $60B AI Data Center Expansion, Starting in Ohio
-

 Science4 months ago
Science4 months agoStarship V3 Set for 2026 Launch After Successful Final Test of Version 2
-

 Technology7 months ago
Technology7 months agoRecovering a Suspended TikTok Account: A Step-by-Step Guide