Technology
Apple Releases Urgent Update to Fix Serious Security Flaw
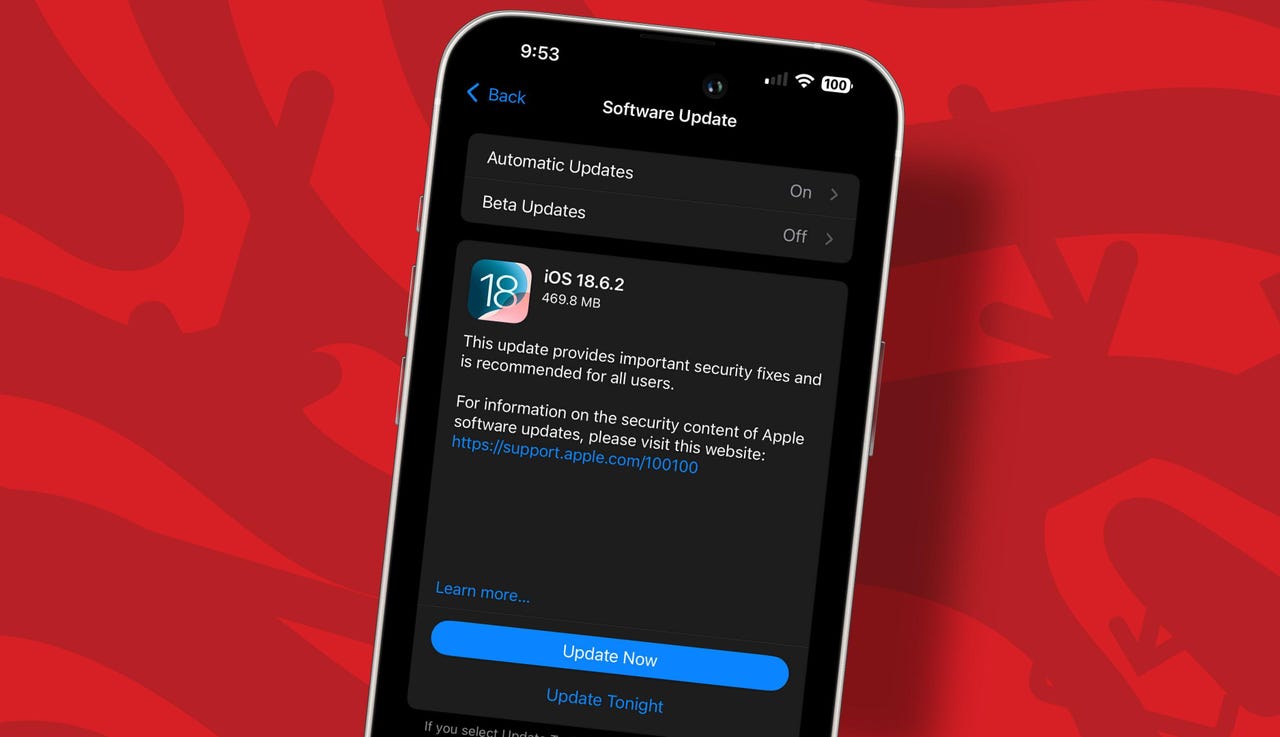
Apple has announced critical updates to its software for the iPhone, iPad, and Mac, addressing a significant security vulnerability that could allow attackers to install spyware. The updates, released on March 15, 2024, specifically target the flaw identified as CVE-2025-43300, which has reportedly been exploited in sophisticated attacks against certain individuals.
The new updates include iOS 18.6.2, iPadOS 18.6.2, iPadOS 17.7.10, and various versions of MacOS, such as Sequoia 15.6.1, Sonoma 14.7.8, and Ventura 13.7.8. Users are urged to install these updates as soon as possible to protect their devices from potential threats.
Understanding the Vulnerability
The flaw resides within Apple’s ImageIO framework, which is responsible for managing image files on Apple devices. According to Apple, “processing a malicious image file may result in memory corruption.” This means that an attacker could craft an image that, when opened, corrupts the device’s memory, allowing them to execute malicious code and potentially install spyware.
The issue is categorized as an “out-of-bounds write issue,” indicating that the flaw permits data to be written outside the allocated memory for a specific application. Apple has implemented “improved bounds checking” to mitigate this risk, ensuring that malicious images cannot exploit this vulnerability.
The implications are serious, as this attack vector could involve seemingly innocuous images. An unsuspecting user might compromise their device simply by viewing a malicious image, making this flaw particularly concerning.
Targeted Attacks and Implications
While Apple emphasizes that the vulnerability has been used in “an extremely sophisticated attack against specific targeted individuals,” the majority of users are unlikely to be affected. This suggests that the flaw may primarily pose a risk to high-profile individuals, such as government officials, political activists, and journalists.
The NSO Group, known for its controversial Pegasus spyware, has been implicated in similar targeted attacks in the past. The group claims its software is intended for use by law enforcement to combat crime and terrorism, yet it has faced numerous allegations of misuse. Apple has taken legal action against NSO Group, reflecting its commitment to enhancing user security.
In the days leading up to this update, Apple also released iOS 18.6.1 and WatchOS 11.6.1, which included new features and improvements. However, the latest update focuses primarily on addressing this critical vulnerability.
For users seeking to update their devices, the process is straightforward. On an iPhone or iPad, navigate to Settings, select General, and tap Software Update. For Mac users, go to System Settings, click on General, and select Software Update.
As cyber threats continue to evolve, staying informed and proactive about software updates is essential for maintaining device security. Users are encouraged to take immediate action to ensure their devices are protected against this serious flaw.
-

 Technology5 months ago
Technology5 months agoDiscover the Top 10 Calorie Counting Apps of 2025
-

 Technology3 weeks ago
Technology3 weeks agoOpenAI to Implement Age Verification for ChatGPT by December 2025
-

 Health3 months ago
Health3 months agoBella Hadid Shares Health Update After Treatment for Lyme Disease
-

 Health4 months ago
Health4 months agoAnalysts Project Stronger Growth for Apple’s iPhone 17 Lineup
-

 Health4 months ago
Health4 months agoErin Bates Shares Recovery Update Following Sepsis Complications
-

 Technology5 months ago
Technology5 months agoDiscover How to Reverse Image Search Using ChatGPT Effortlessly
-

 Technology3 months ago
Technology3 months agoElectric Moto Influencer Surronster Arrested in Tijuana
-

 Technology5 months ago
Technology5 months agoMeta Initiates $60B AI Data Center Expansion, Starting in Ohio
-

 Technology2 months ago
Technology2 months agoDiscover 2025’s Top GPUs for Exceptional 4K Gaming Performance
-

 Technology5 months ago
Technology5 months agoRecovering a Suspended TikTok Account: A Step-by-Step Guide
-

 Health5 months ago
Health5 months agoTested: Rab Firewall Mountain Jacket Survives Harsh Conditions
-

 Lifestyle5 months ago
Lifestyle5 months agoBelton Family Reunites After Daughter Survives Hill Country Floods