Technology
Switching from Cloudflare to Tailscale: A Frustrating Experience

The attempt to switch from Cloudflare Tunnels to Tailscale has proven to be a frustrating experience, particularly due to the limitations imposed by a managed Wi-Fi environment. While both services aim to solve similar networking challenges, their approaches differ significantly. After years of using Cloudflare, which seamlessly handled network restrictions without requiring adjustments from my Wi-Fi provider, the move to Tailscale initially appeared promising. However, this transition did not meet expectations for public service accessibility.
Understanding the Network Limitations
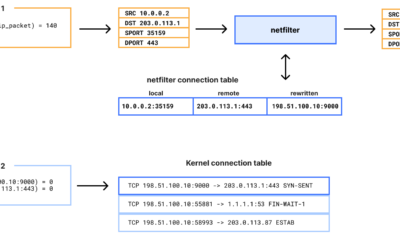
My apartment utilizes a managed Wi-Fi system that conceals each resident behind carrier-grade NAT (CGNAT). This configuration limits my access to the modem and router, preventing any port forwarding—a critical aspect for hosting services. Cloudflare Tunnels effectively navigated this issue by leveraging an outbound connection from my server to Cloudflare’s network, allowing for straightforward public access. In contrast, Tailscale’s approach is different and proved inadequate for my specific needs.
Tailscale’s Funnel feature aims to expose services publicly but is not universally available across all platforms. While it excels at establishing secure private connections, it falters when attempting to provide public access. My initial attempt to migrate Nextcloud, which is essential for remote access, highlighted these shortcomings. Rather than being accessible from the open internet, my Nextcloud instance was confined to the Tailscale network, limiting its utility.
The troubleshooting process revealed that the issues stemmed from Tailscale’s inherent design rather than configuration errors. The service focuses on private communications between authenticated devices on a tailnet, which complicates public access for users who do not wish to install additional clients or authenticate.
Cloudflare’s Superior Public Access
In contrast, Cloudflare Tunnels offered a seamless experience by establishing an outbound connection via the cloudflared daemon. This connection, which operates on port 443, facilitated instant loading of my Nextcloud instance from outside my network. The simplicity of this setup—requiring no special approvals or adjustments from building management—demonstrated Cloudflare’s effectiveness in providing a stable public entry point.
While Tailscale is an impressive tool for private networking, it does not cater to my need for public-facing services. The restricted environment of my managed Wi-Fi system ultimately dictated that Tailscale could not fulfill the requirements necessary for effective service hosting.
Despite these challenges, Tailscale impressed with its capabilities in other areas. The private device-to-device connections were quick and secure, leveraging the WireGuard protocol for a responsive experience. This performance is ideal for sensitive internal tools or quick remote access, showcasing Tailscale’s strengths in private networking.
Yet, for users like myself who require services to be publicly accessible, Tailscale’s current model falls short. The need for broader availability of the Funnel feature and a more flexible public access model is critical for Tailscale to compete effectively with Cloudflare in restrictive environments.
The potential for improvement lies in Tailscale’s ability to adopt a public access layer that does not mandate users to join a tailnet. Such modifications would significantly enhance its usability in scenarios where public reachability is paramount.
Future Considerations for Network Control
An alternative solution to my networking challenges would be to switch my internet service provider. If my apartment complex allowed residents to utilize their own internet service, I would regain full control over my network. This change would eliminate CGNAT, enabling port forwarding and allowing me to choose how my services are exposed.
With this control, Tailscale could effectively provide private connectivity while traditional solutions like Cloudflare would manage public access. The ability to select networking equipment would further streamline my home lab configuration, allowing for a more tailored setup without compromise.
In summary, the attempt to transition from Cloudflare Tunnels to Tailscale has highlighted the limitations of Tailscale in environments with strict network conditions. While Tailscale excels in private connectivity, Cloudflare remains the optimal choice for exposing services in my specific case. Until Tailscale enhances its public access capabilities or my network environment changes, Cloudflare continues to address the pressing needs of my home lab effectively.
-

 Science1 month ago
Science1 month agoNostradamus’ 2026 Predictions: Star Death and Dark Events Loom
-

 Technology2 months ago
Technology2 months agoOpenAI to Implement Age Verification for ChatGPT by December 2025
-

 Technology7 months ago
Technology7 months agoDiscover the Top 10 Calorie Counting Apps of 2025
-

 Health5 months ago
Health5 months agoBella Hadid Shares Health Update After Treatment for Lyme Disease
-

 Health5 months ago
Health5 months agoAnalysts Project Stronger Growth for Apple’s iPhone 17 Lineup
-

 Technology5 months ago
Technology5 months agoElectric Moto Influencer Surronster Arrested in Tijuana
-

 Science2 months ago
Science2 months agoBreakthroughs and Challenges Await Science in 2026
-

 Education5 months ago
Education5 months agoHarvard Secures Court Victory Over Federal Funding Cuts
-

 Health5 months ago
Health5 months agoErin Bates Shares Recovery Update Following Sepsis Complications
-

 Technology7 months ago
Technology7 months agoMeta Initiates $60B AI Data Center Expansion, Starting in Ohio
-

 Technology6 months ago
Technology6 months agoDiscover How to Reverse Image Search Using ChatGPT Effortlessly
-

 Science4 months ago
Science4 months agoStarship V3 Set for 2026 Launch After Successful Final Test of Version 2